How to find the MAC address of a Windows PC on a remote subnet
A colleague and I both work on a number of our systems using two different approaches; I will often go for a more technically creative approach, whereas he will often find something that exists which gets the job done. The great thing about his approach is that he has some very cool tools that do some interesting and useful things, but I like to try and find out the more technical side of them and work out why they do what they do.
A critical point for me – and my wanting to understand everything – was reached recently when he showed me SoftPerfect Network Scanner. This tool can show you all active hosts in a given network range – something like nmap perhaps, but you can also use it to send WOL packets and remotely connect to a given machine. This is great stuff, and it doesn’t elude me how these two things are accomplished, but what really bugge my mind was how this tool could find not only a hostname, but that system’s MAC address too!
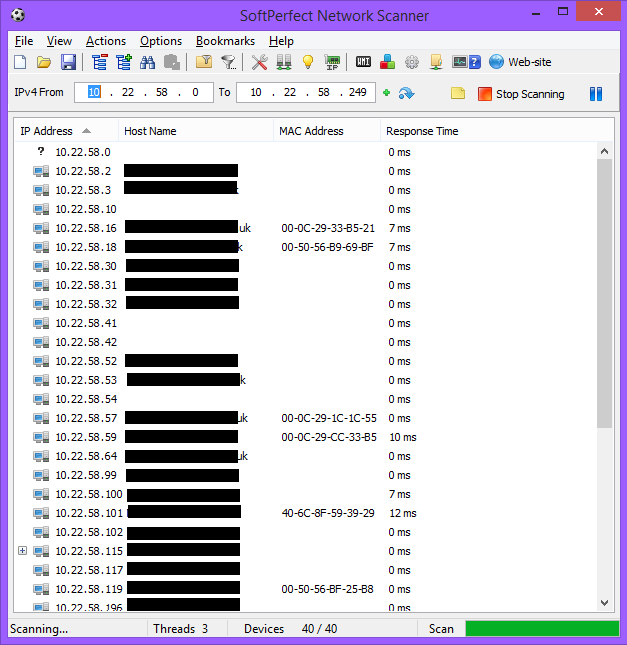
Anyone who knows about networking would probably agree that you can only learn about the MAC addresses of neighbouring machines on the same local subnet (broadcast domain). You can do this by performing an arp/rarp lookup on known hosts and this information is stored in a table. But since you communicate on layer 3 – IP addresses and all that stuff – between subnets, how on earth can you find out a system’s MAC address from a remote subnet? Because the screenshot above shows hosts that are even routed from a different network entirely.
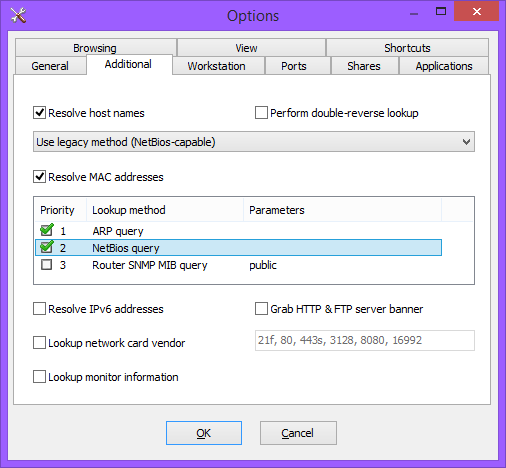
There is one odd thing though; the only clients that actually show off their MAC address are all Windows machines (and an Apple Mac server!). Then, after using trusty Wireshark, I found out the cause and you can have a look in the options menu of Network Scanner too and find out how it does it; it uses a mixture of ARP and NetBIOS.
Wireshark reliably informed me that it uses NBSTAT packets to send and receive information on port 137. In essence, if a machine is running Windows, it seems to just responds to anyone who queries it for its hostname and MAC addresses – and it can even be used to find out who is logged in, too.
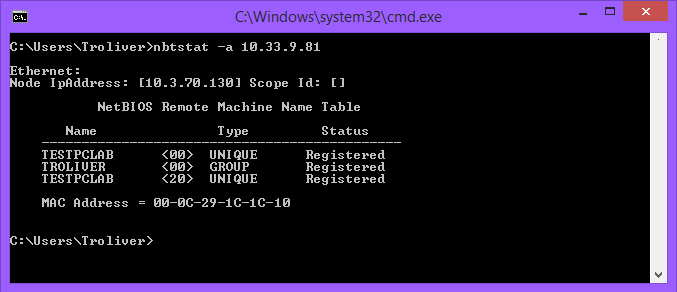
So if you want to try this yourself, you can use the command nbtstat from the command line in Windows (where xxx.xxx.xxx.xxx is the address of the machine you want to find the MAC address of):
nbtstat -a xxx.xxx.xxx.xxx
Note that this will fail if the remote firewall blocks port 137 – which Windows Server does by default.
Here you can see that the remote PC – TESTPCLAB – is on the TROLIVER domain with its MAC address available to all who may want to probe on port 137! Hopefully someone will find this useful for finding MACs too, securing PCs, or just as an interesting use of NetBIOS.
‹ FOG – Installing and Troubleshooting FOG 1.2.0 on Ubuntu 14.04 Progress update: network mapping tool thing ›
This is so useful!!! Well done.